What Is End-to-End Encryption? Why It Matters for Cloud Security
In today’s digital world, where data breaches and cyber threats are increasing, protecting sensitive information has never been more crucial. It’s important to ensure that your data is secure and private. End-to-End Encryption (E2EE), is a powerful security tool that can prevent unauthorized access even when your files are stored on the cloud.
End-to-end encryption (E2EE) is a method of securing data so that it remains fully encrypted from the moment it leaves your device until it reaches the intended recipient. Only the sender and the authorized receiver have the decryption key, ensuring that no third party including hackers, internet service providers, or even the cloud storage provider can access the contents.

Unlike traditional encryption, where data may be decrypted at certain points during transmission, E2EE ensures that your files remain protected throughout the entire process. It is one of the safest ways to share and store sensitive information.
What Is End-to-End Encryption (E2EE) in Simple Terms?
E2EE (End-to-End Encryption) is a method of security that only allows the sender to access data transmitted. Even if data is intercepted, the recipient, service provider, or hackers cannot read it.
Think of E2EE as a locked mailbox:
This encryption process ensures maximum privacy and security, making it ideal for sensitive data like financial transactions, private messages, and personal files.
Why Is Data Security Crucial in Cloud Storage?
Cloud storage has become an essential tool for storing, accessing, and sharing files across multiple devices. However, storing data in the cloud comes with security risks:
By implementing end-to-end encryption, cloud storage services ensure that even if a data breach occurs, the encrypted files remain unreadable to unauthorized parties.
How Popular Cloud Services Implement Encryption
Many cloud storage services provide encryption in different forms, but not all offer true end-to-end encryption:
Understanding how different cloud providers handle encryption helps you choose the most secure option for storing your sensitive files.
How Does End-to-End Encryption Work?
E2EE follows a simple yet powerful process to keep data secure:
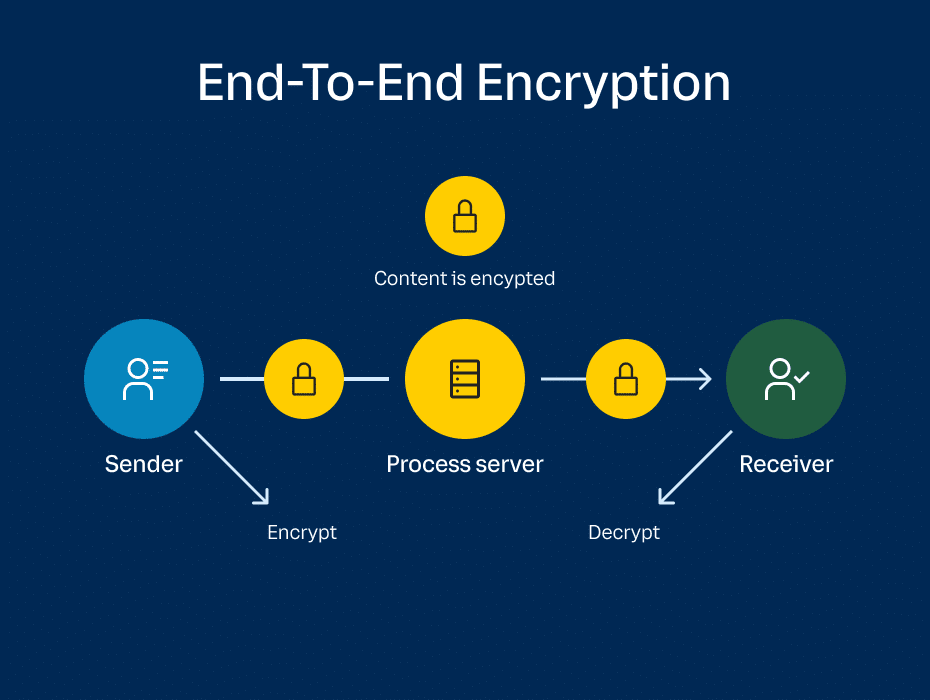
1. Encryption at the Sender’s Side
- Before leaving your device, the data is converted into an unreadable format using a cryptographic key.
- Only the intended recipient has the private key to decrypt it.
2. Secure Transmission
- The encrypted data is sent over the internet, protected from hackers and third-party access.
- Even if someone intercepts the data, it remains completely scrambled and unusable.
3. Decryption at the Receiver’s Side
- The intended recipient uses their private decryption key to restore the data to its original form.
- No one else not even the service provider can access the decrypted data.
This process ensures only authorized users can read or access the data, making it one of the most secure encryption methods available.
How Is E2EE Different from Other Encryption Methods?
Most cloud storage services use some form of encryption, but not all encryption methods are equal. Here’s how E2EE differs from standard encryption techniques:
|
Encryption Type |
How It Works |
Who Can Access Data? |
Security Level |
|---|---|---|---|
|
End-to-End Encryption (E2EE) |
Data is encrypted before leaving the sender’s device and only decrypted by the recipient. |
Only sender & recipient (not even the service provider). |
Highest Security |
|
Encryption in Transit |
Data is encrypted while being transmitted, but decrypted when it reaches the server. |
Cloud provider can access stored data. |
Moderate Security |
|
Encryption at Rest |
Data is stored in an encrypted format on the provider’s servers. |
Cloud provider can access data and decrypt it if needed. |
Lower Security |
Key Takeaways:
- E2EE is the most secure encryption method because no third party can access the data not even the cloud provider.
- Encryption in transit and at rest protect data to some extent, but the cloud provider can still access it if needed.
- For maximum privacy, choose cloud storage providers that offer built-in E2EE (like MEGA or Sync.com).
By understanding these differences, users can make informed decisions about which cloud storage services truly protect their sensitive data.
Which Cloud Storage Services Use End-to-End Encryption?
Cloud storage services do not all offer end-to-end (E2EE) encryption. Many only use basic encryption techniques that do no protect data. Others prioritize privacy and security, while some services are geared towards convenience. Here’s a breakdown on how the major cloud storage services handle encryption, and which ones keep your data truly private.

Cloud Storage Services Without EE2E
Here are some cloud storage services without End-to-End Encryption:
1. Google Drive
It can encrypt files while in transit or at rest but cannot provide end-to-end encryption. This means Google can access your data, and scan the files to be used for targeted advertising or security.

2. TeraBox
It is also lacking end-to-end security. provides basic encryption. However, privacy has been a concern, since the service is owned and operated by a Chinese firm. Its main focus is providing large free storage rather than high level security features. Click Here to download terabox premium for free.

3. Microsoft OneDrive
OneDrive is able to encrypt files while they are in transit and at rest. however, does not support E2EE as a default. Microsoft has access to the files stored, and Personal vault does add extra security. However, is not a true E2EE Solution.

2. Cloud Storage Services With EE2E
Cloud storage providers that prioritize privacy and security implement end-to-end (E2EE) encryption, ensuring only the user can access their files.
These providers are not able to access, scan or decrypt data stored, which makes them a preferred option for users who care about data security.
Tresorit: offers full end-to-end encryption, meaning that files are encrypted before they leave the user’s device. Since Tresorit has no access to the encryption keys, even the company itself cannot read or decrypt user data. This makes it one of the most secure cloud storage solutions available.
Sync.com: follows a zero-knowledge encryption policy, ensuring that only the user can decrypt and access their files. Even Sync.com’s own servers cannot read the stored data, providing an additional layer of security against cyber threats or unauthorized access.
MEGA: offers automatic end-to-end encryption, guaranteeing that all uploaded files remain private and inaccessible to the service provider. This ensures that user data stays secure, even in the event of a security breach.
Conclusion
End-to end encryption (E2EE), is the best way to protect sensitive data against unauthorized access. Many popular cloud storage services, such as Google Drive, OneDrive and TeraBox, offer encryption both at rest and during transit. However, they don’t provide true E2EE. This means that your data could still be accessible by the service provider.
Cloud services such as Tresorit, Sync.com and MEGA, which prioritize privacy and security for their users, offer end-to-end encrypted files. This ensures that only you have access to your files. Choose a cloud service that offers E2EE to ensure your data is protected, even if there’s a breach.